Videos
Check out our tutorial video series.
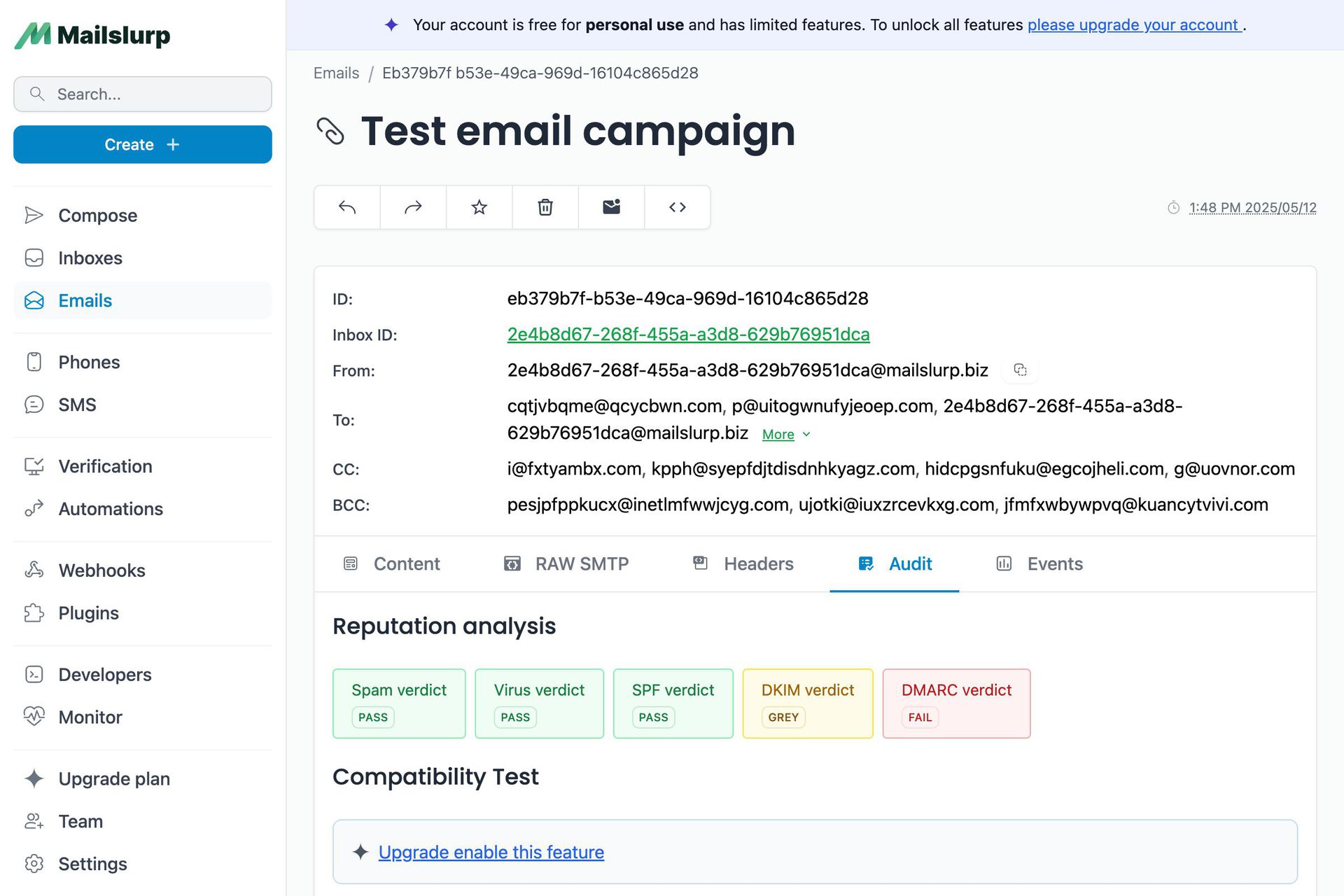
A Domain-based Message Authentication Reporting and Conformance (DMARC) record consists of numerous tags.
DNS record is a type of TXT record published in the DNS of a domain, containing policies and instructions for handling emails that fail SPF and DKIM checks. This record helps in mitigating email spoofing and phishing by providing email receivers with a mechanism to authenticate the messages, enhancing email deliverability and security.
DMARC, which stands for Domain-based Message Authentication Reporting and Conformance, is an email protocol that uses SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) to ascertain the authenticity of an email message. It aims to prevent email-based abuse, such as phishing and spoofing, which are often used in cyber-attacks.
DMARC works by allowing domain owners to publish policies in their DNS records that define their email authentication practices and provide instructions for receiving mail servers (such as Gmail, Yahoo, etc.) on how to handle emails that fail the checks. These instructions can guide the receiver to either quarantine or reject non-authenticated emails, helping to protect both the sender's reputation and the recipient's security.
For assistance in formulating a DMARC record, MailSlurp's DMARC Record Assistant can be of use or read on. DMARC records are basically DNS TXT records that have the name and the value something like .
To validate your DKIM tag use the MailSlurp DMARC validation tool.
Check out our tutorial video series.
Email and SMS guides for automation and testing.
View github project code for multiple languages.
Latest posts from the MailSlurp team.
Test, build, and automate messaging with a free MailSlurp account.